How to create and manage the ransomware policy?
Follow these steps to setup and manage the ransomware policy in SysCloud Safety, Security & Compliance App:
-
Log in to the SysCloud Application with your account credentials.
- Click “Safety, Security & Compliance”→“Create Policy.”
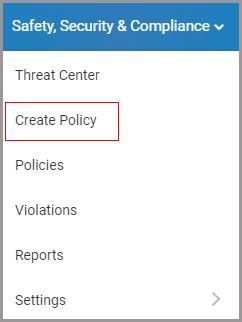
- Click “Ransomware” on the left pane.
- Click on the “COPY AND ACTIVATE POLICY” for instant policy activation. To customize the policy select the “VIEW AND EDIT POLICY” option.
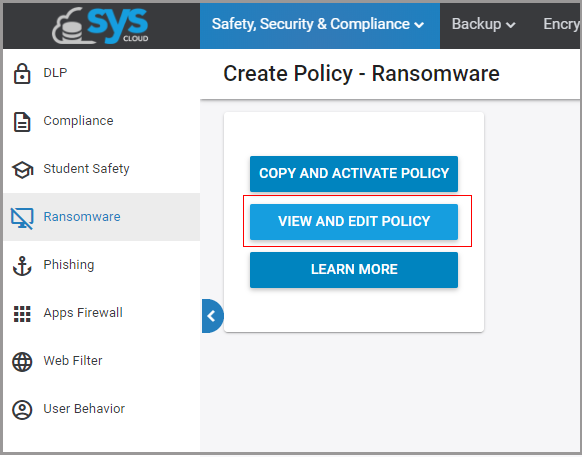
- Create a name for the ransomware policy.
- Select the scope for the policy: users, groups, org units, or the entire domain, and click “NEXT.”
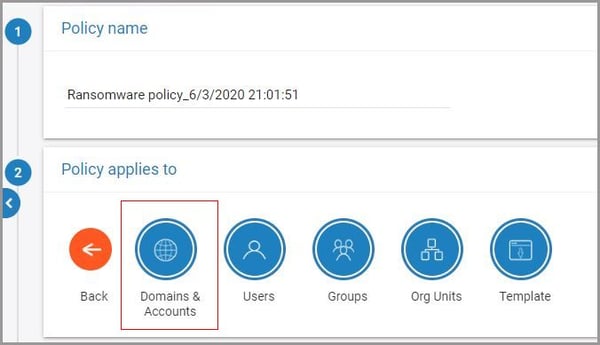
7. Select the accounts where the policy needs to be applied and click “NEXT.”
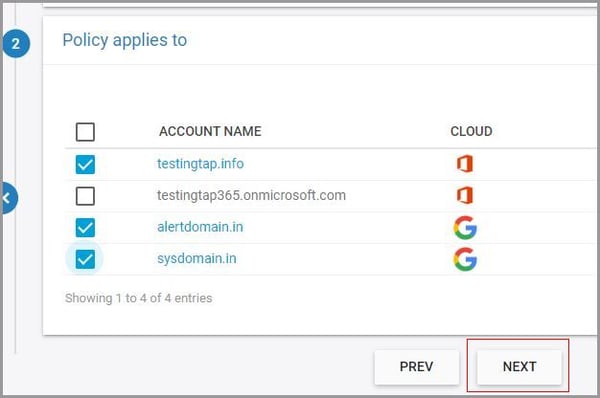
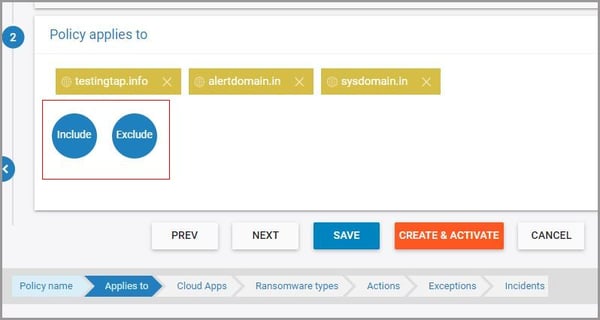
8. Choose additional domains, user, or org units to be excluded or included in the scope of the policy and click “NEXT.”
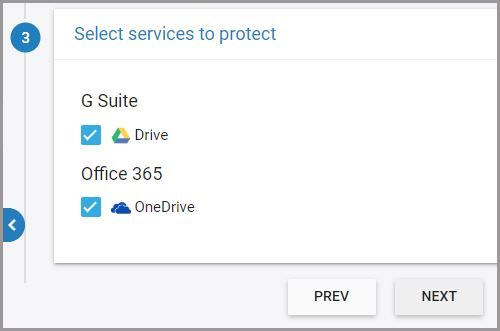
9. Select the cloud service to protect – you can choose Google Drive, OneDrive, or both – and click “NEXT.”
10. Choose the ransomware file types to scan and click “NEXT.”
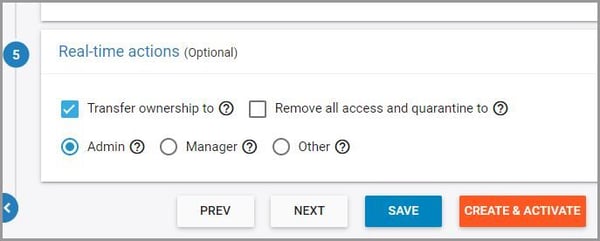
11. Select one or both the real-time actions for ransomware violations:
-
- Transfer file ownership to another user
- Remove all access and quarantine files
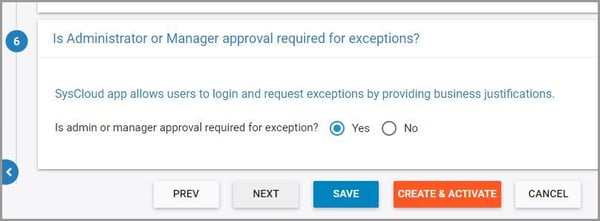
12. Select whether you want to allow users to request exceptions on policy violations and click “Next.”
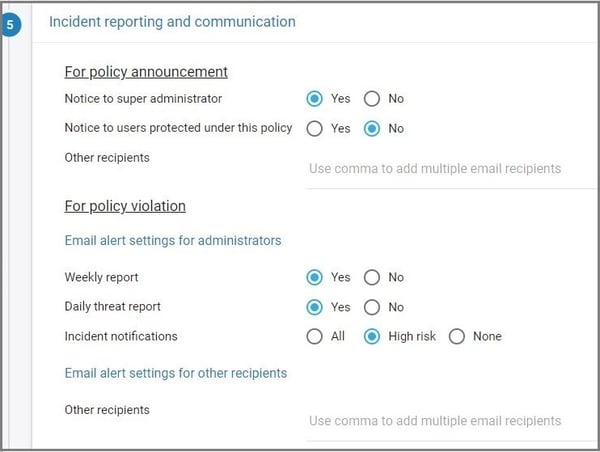
13. Choose the team members to be notified in case of policy violations. You can also select whether the policy violations need to be included in the weekly and daily threat reports.
14. Click “CREATE & ACTIVATE.”

Once the policy is active you will receive violation alerts based on your policy settings. Follow these steps to view and manage policy violations:
- Navigate to “Safety, Security & Compliance”→“Violations.”
2. Select “Ransomware” on the left pane.
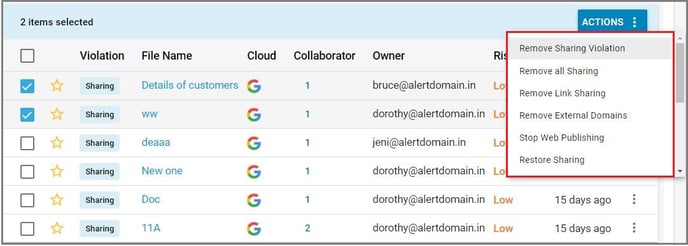
3. Click on the vertical ellipses on the right-hand side of the screen to view the violation or to share it with another user.
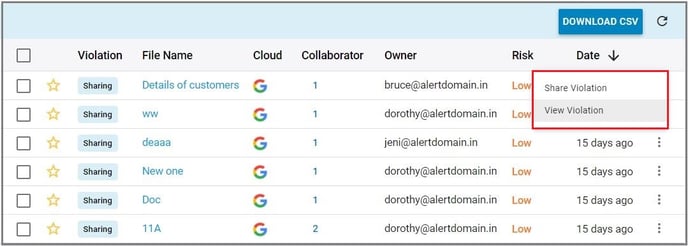
4. Select one or more violation(s) to perform the following actions:
-
- Remove all sharing
- Remove link sharing
- Remove external domains
- Restore sharing
- Take control from the owner
- Apply encryption
- Dismiss
- Remove all access and quarantine